Braindump2go Guarantees Your Microsoft 70-341 Exam 100% Success with Our Unique Official 70-341 Exam Questions Resources! Braindump2go’s 70-341 Braindumps are Developed by Experiences IT Certifications Professionals Working in Today’s Prospering Companies and Data Centers! Braindump2go 70-341 Exam Dumps are Checked by Our Experts Team every day to ensure you have the Latest Updated Exam Dumps!
Vendor: Microsoft
Exam Code: 70-341
Exam Name: Microsoft Core Solutions of Microsoft Exchange Server 2013
Keywords: 70-341 Exam Dumps,70-341 PDF Download,70-341 VCE Download,70-341 Study Guide,70-341 Study Material,70-341 Braindump,70-341 Exam Questions,70-341 Book
QUESTION 11
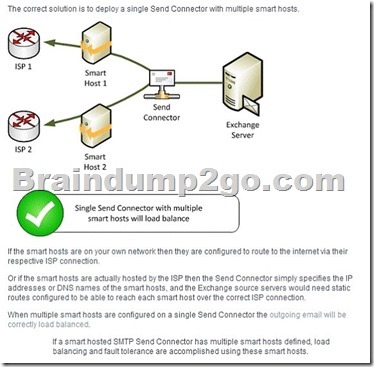
You need to recommend a temporary solution to reroute all of the outbound email messages through the Miami mail appliance during the planned replacement of the New York mail appliance.
What are three possible ways to achieve the goal? (Each correct answer presents a complete solution. Choose three.)
A. Modify the value of the SmartHost of the Send connector in the New York office.
B. Increase the cost of the Send connector in the Miami office.
C. Increase the cost of the Send connector in the New York office.
D. Decrease the cost of the Send connector in the New York office,
E. Modify the value of the SmartHost of the Send connector in the Miami office.
F. Disable the Send connector in the New York office.
Answer: ACF
Explanation:
Both Miami and New York have external connections to the internet with Client Access Servers
In Microsoft Exchange Server 2013, a Send connector controls the flow of outbound messages to the receiving server
Internal Send connectors send e-mail to servers in your Exchange organization. This connector is configured to route e-mail to your internal Exchange servers as smart hosts. A smart host (also known as a relay host) is a server that redirects outbound mail. Send connectors send e-mail to the Internet. This connector is configured to use Domain Name System (DNS)
MX records to route e-mail.
The cost is important if there is more than one connector that can be used, where the lower the cost the more preferred the route.
This is useful if you have two Internet connections, and only want to use the slower one when the faster is down. Like weights in SRV records, the values are arbitrary. 1 vs 10 is no different than 1 vs 2, as long as there are no others you want to squeeze between them.
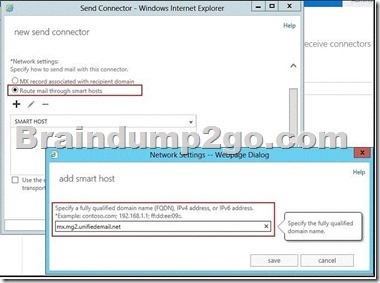
Smart Host
In some situations you may want to route email through a third-party smart host, such as in an instance where you have a network appliance that you want to perform policy checks on outbound messages.
A smart host is a type of email message transfer agent which allows an SMTP server to route email to an intermediate mailserver rather than directly to the recipient’s server. Often this smart host requires authentication from the sender to verify that the sender has privileges to have mail forwarded through the smart host. This is an important distinction from an open mail relay that will forward mail from the sender without authentication. Common authentication techniques include SMTP Authentication and POP before SMTP.
When configured to be a backup mail server (not the primary MX record), a smart host configuration will accept mail on behalf of the primary mail server if it were to go offline. When the primary mail server comes back online, mail is subsequently delivered via the smart host.
Some ISPs, in an effort to reduce email spam originating at their customer’s IP addresses, will not allow their customers to communicate directly with the recipient’s mail server via the default SMTP port number 25. In this case the customer has no choice but to use the smart host provided by the ISP.
When a host runs its own local mail server, a smart host is often used to transmit all mail to other systems through a central mail server. This is used to ease the management of a single mail server with aliases, security, and Internet access rather than maintaining numerous local mail servers.
NOT B
Need to increase the cost of the Send Connect in the New York Office
NOT D
Need to increase the cost not decrease the cost of the Send Connector in the New York Office
NOT E
Need to modify the value of the SmartHost of the Send connector in the New York office
A
Modify the value of the SmartHost of the Send connector in the New York office to point to the smart host in the Miami office.
C
Increasing the cost of a Send Connector in the New York Office will make the Miami connection to the internet the most preferred outbound connection.
F
Disabling the Send connector in the New York Office will make the Miami connection to the internet the only outbound connection.
QUESTION 12
Hotspot Question
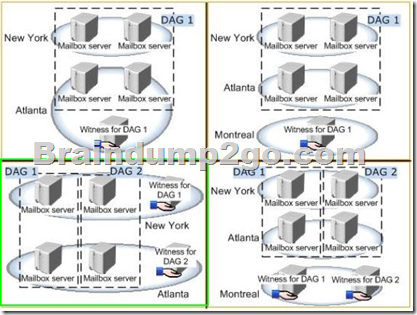
You are evaluating a DAG design for the New York and Atlanta offices.
You need to ensure that all of the users in the New York and Atlanta offices can access their mailbox if the WAN link fails.
Which DAG design should you deploy? To answer, select the appropriate DAG design in the answer area.
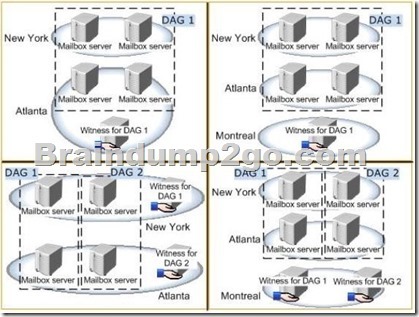
Answer:
QUESTION 13
Hotspot Question
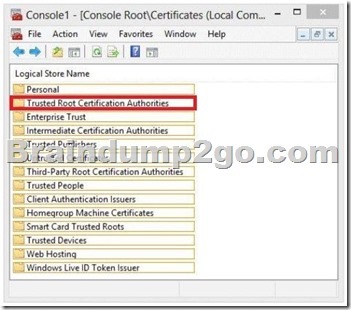
You discover that one of the Client Access servers in the New York office does not trust the standalone CA.
You need to ensure that all of the users who have Windows Phone devices can connect successfully to their mailbox.
In which node should you install the root CA certificate? To answer, select the appropriate node in the answer area.
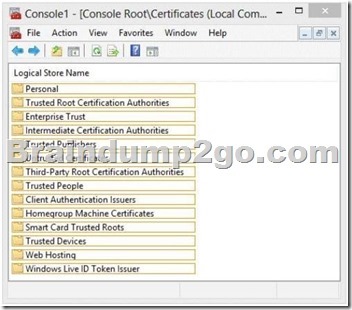
Answer:
QUESTION 14
You plan to deploy an Exchange Server 2013 organization.
You need to recommend a solution to ensure that a user named User1 can access email messages by using Exchange ActiveSync on an Android device.
The solution must prevent all other users from using Android devices to access email by using Exchange ActiveSync.
What should you recommend doing first?
A. Run the Set-CasMailbox cmdlet.
B. Create a device access rule.
C. Modify the Quarantine Notification settings.
D. Create a mobile device mailbox policy.
Answer: B
Explanation:
Access the Allow/Block/Quarantine rules
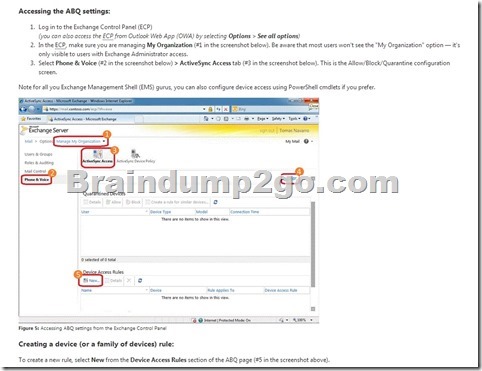
NOT A
Use the Set-CASMailbox cmdlet to set attributes related to client access for Microsoft Exchange ActiveSync, Microsoft Office Outlook Web App, POP3, and IMAP4 for a specified user.
The Set-CASMailbox cmdlet operates on one mailbox at a time. You can configure properties for Outlook Web App, Exchange ActiveSync, POP3, and IMAP4 by using this cmdlet.
You can configure a single property or multiple properties by using one statement.
Need to create a rule to allow a particular user to use Exchange ActiveSync on an Android device.
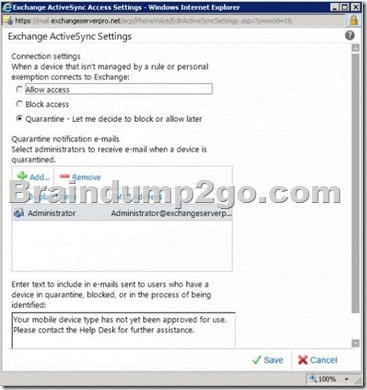
NOT C
Can allow or block access for all users.
Quarantine all uses and then selectively allow the users access.
A new device rule is a better way of managing the problem.
NOT D
Need a policy for a single user.
In Microsoft Exchange Server 2013, you can create mobile device mailbox policies to apply a common set of policies or security settings to a collection of users. After you deploy Exchange ActiveSync in your Exchange 2013 organization, you can create new mobile device mailbox policies or modify existing policies. When you install Exchange 2013, a default mobile device mailbox policy is created. All users are automatically assigned this default mobile device mailbox policy.
Case Study 2: Litware, Inc (QUESTION 15 ~ QUESTION 21)
Overview
Litware, Inc., is a manufacturing company located in North America.
The company has a main office and two branch offices.
The main office is located in Chicago.
The branch offices are located in Baltimore and Los Angeles.
Existing Environment
Active Directory Environment
The network contains one Active Directory forest named litwareinc.com. Each office is configured as an Active Directory site. All domain controllers in the Los Angeles office run Windows Server 2008 R2. All domain controllers in the Chicago office run Windows Server 2003 Service Pack 1 (SP1). All domain controllers in the Baltimore office run Windows Server 2012. All of the FSMO roles are located on a domain controller in the Baltimore office. All of the domain controllers are configured as global catalog servers. You have a distribution group for each department. The distribution groups contain all of the users in each respective department.
Network Infrastructure
The servers in each office are configured as shown in the following table.
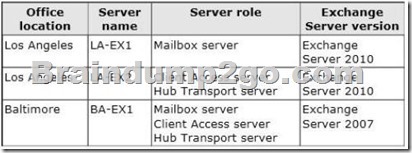
The Baltimore and Chicago offices have independent Internet connections. Internet connectivity for the Los Angeles office is provided through Chicago. Users frequently send large email messages to other users in the company. Recently, you increased the maximum message size to 50 MB.
Planned Changes
The company plans to deploy a new Exchange Server 2013 infrastructure that will contain two Clients Access servers and two Mailbox servers in the Chicago office.
The servers will be configured as shown in the following table.
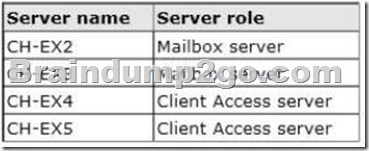
All client connections to the Exchange Server organization will be routed through a hardware load balancer. The name client.litwareinc.com will point to the virtual IP address of the hardware load balancer. Once the transition to Exchange Server 2013 in the Chicago office is complete, all mail flow to and from the Internet will be managed centrally through that office by using a Send connector that has the following configurations:
– Connector name: CH-to-Internet
– Address space: *
– Source servers: CH-EX2, CH-EX3
– Cost: 10
QUESTION 15
You need to recommend changes to the network to ensure that you can deploy the planned Exchange Server 2013 infrastructure.
What should you recommend?
A. Transfer of the FSMO roles to a domain controller in the Chicago office.
B. Change the forest functional level.
C. Change the domain functional level.
D. Change the operating system on one of the domain controllers in the Chicago office
Answer: D
Explanation:
DIFFICULT QUESTION
FSMO ( Flexible Single Master Operations )
In a forest, there are five FSMO roles that are assigned to one or more domain controllers.
The five FSMO roles are:
Schema Master:
The schema master domain controller controls all updates and modifications to the schema. Once the Schema update is complete, it is replicated from the schema master to all other DCs in the directory. To update the schema of a forest, you must have access to the schema master. There can be only one schema master in the whole forest.
Domain naming master:
The domain naming master domain controller controls the addition or removal of domains in the forest. This DC is the only one that can add or remove a domain from the directory. It can also add or remove cross references to domains in external directories. There can be only one domain naming master in the whole forest.
Infrastructure Master:
When an object in one domain is referenced by another object in another domain, it represents the reference by the GUID, the SID (for references to security principals), and the DN of the object being referenced. The infrastructure FSMO role holder is the DC responsible for updating an object’s SID and distinguished name in a cross-domain object reference. At any one time, there can be only one domain controller acting as the infrastructure master in each domain.
Note: The Infrastructure Master (IM) role should be held by a domain controller that is not a Global Catalog server (GC). If the Infrastructure Master runs on a Global Catalog server it will stop updating object information because it does not contain any references to objects that it does not hold. This is because a Global Catalog server holds a partial replica of every object in the forest. As a result, cross-domain object references in that domain will not be updated and a warning to that effect will be logged on that DC’s event log. If all the domain controllers in a domain also host the global catalog, all the domain controllers have the current data, and it is not important which domain controller holds the infrastructure master role.
Relative ID (RID) Master:
The RID master is responsible for processing RID pool requests from all domain controllers in a particular domain. When a DC creates a security principal object such as a user or group, it attaches a unique Security ID (SID) to the object. This SID consists of a domain SID (the same for all SIDs created in a domain), and a relative ID (RID) that is unique for each security principal SID created in a domain. Each DC in a domain is allocated a pool of RIDs that it is allowed to assign to the security principals it creates. When a DC’s allocated RID pool falls below a threshold, that DC issues a request for additional RIDs to the domain’s RID master. The domain RID master responds to the request by retrieving RIDs from the domain’s unallocated RID pool and assigns them to the pool of the requesting DC. At any one time, there can be only one domain controller acting as the RID master in the domain.
PDC Emulator:
The PDC emulator is necessary to synchronize time in an enterprise.
The PDC emulator of a domain is authoritative for the domain. The PDC emulator at the root of the forest becomes authoritative for the enterprise, and should be configured to gather the time from an external source.
All PDC FSMO role holders follow the hierarchy of domains in the selection of their in-bound time partner.
NOT A
All of the FSMO roles are located on a domain controller in the Baltimore Office. All of the domain controllers are configured as a global catalog server
No need to transfer all of these roles to the chicago domain controller as the question suggests.
NOT B
Apparently no need to change the forest functional level http://technet.microsoft.com/en-us/library/cc771294.aspx
Forest functional levels enable features across all the domains in your forest. The following table lists the forest functional levels and their corresponding supported domain controllers.
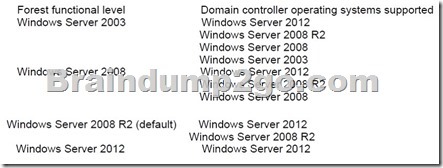
NOT C
Apparently no need to change the domain functional level http://technet.microsoft.com/en-us/library/cc771294.aspx
For all domain controllers to function accordingly in the domain the domain functional level would have to be set to Windows Server 2003
All domain controllers in the Chicago office run Windows Server 2003 Service Pack 1.
(SP1)
All domain controllers in the Los Angeles office run Windows Server 2008 R2.
All domain controllers in the Baltimore office run Windows Server 2012
Domain functional levels
Domain functionality enables features that affect the entire domain and that domain only.
The following table lists the domain functional levels and their corresponding supported domain controllers:
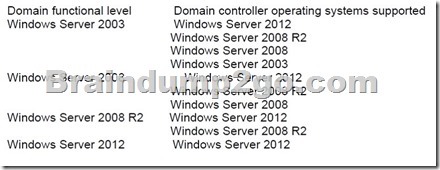
D
http://technet.microsoft.com/en-us/library/ff728623(v=exchg.150).aspx
Mixture of exchange 2007,2010 and 2013 environment
Exchange 2007/2010/2013 can operate in a Windows Server 2003/2008/2012 domain functional level Exchange 2007/2010/2013 can operate in a Windows Server 2003/2008/2012 forest functional level However to operate appropriately the min spec for Exchange 2013 is for an AD environment of Server 2003 SP2
Currently all of the chicago domain controllers are 2003 SP1
Need to upgrade a chicago domain controller which will house Exchange 2013
QUESTION 16
Hotspot Question
You need to identify which names must be used as the URLs of each virtual directory on the planned Exchange Server 2013 servers.
Which names should you identify? To answer, configure the appropriate name for each server in the answer area.
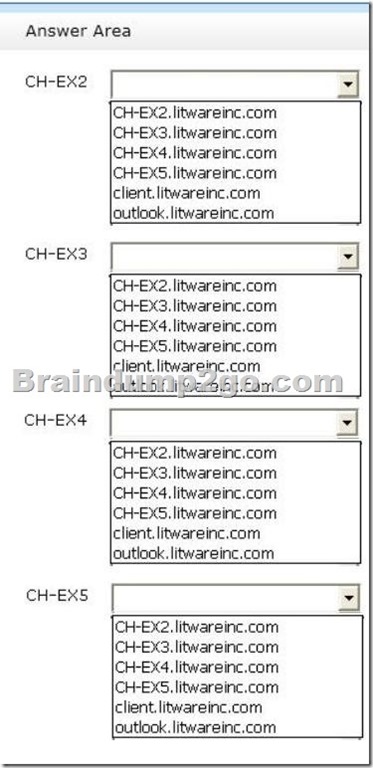
Answer:
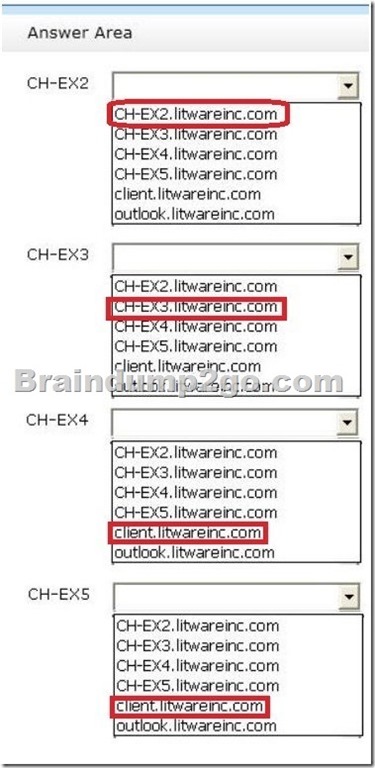
QUESTION 17
You need to recommend which tasks must be performed to deliver email messages to the Internet if CH-EX2 and CH-EX3 fail to connect to the Internet.
The solution must ensure that all queued email is sent.
Which two tasks should you recommend? (Each correct answer presents part of the solution. Choose two.)
A. Run the retry-queue ch-to-internet command.
B. Create a new Send connector on a server in the Baltimore office,
C. Modify the cost of the CH-to-Internet Send connector.
D. Run the set-sendconnector -identity ch-to-internet -frontendproxyenabled Strue command.
E. Disable the CH-to-Internet Send connector.
Answer: BE
Explanation:
The Baltimore and Chicago offices have independent Internet connections. Internet connectivity for the Los Angeles office is provided through Chicago.
Currently no mail servers in Chicago.Only in Baltimore and Los Angeles.
Once the transition to Exchange Server 2013 in the Chicago office is complete, all mail flow to and from the Internet will be managed centrally through that office by using a Send connector that has the following configurations:
– Connector name: CH-to-Internet
– Address space *
– Source servers: CH-EX2, CH-EX3
– Cost: 10
When you deploy Exchange 2013, outbound mail flow cannot occur until you configure a Send connector to route outbound mail to the Internet.
NOT A
Will not resolve the issue.
Use the Retry-Queue cmdlet to force a connection attempt for a queue on a Mailbox server or an Edge Transport server.
EXAMPLE 1
This example forces a connection attempt for all queues that meet the following criteria:
The queues are holding messages for the domain contoso.com.
The queues have a status of Retry.
The queues are located on the server on which the command is executed.
Retry-Queue -Filter {NextHopDomain -eq “contoso.com” -and Status -eq “Retry”}
NOT C
Modifying the cost will not fix the issue of CH-EX2 and CH-EX3 failing to connect to the Internet.
Cost is used to set the priority of this connector, used when two or more connectors are configured for the same address space. The lower the cost higher the priority.
NOT D
Modifying the send connector will not fix the internet connection from chicago mail server to the internet.
Use the Set-SendConnector cmdlet to modify a Send connector.
EXAMPLE 1
This example makes the following configuration changes to the Send connector named Contoso.com Send Connector:
Sets the maximum message size limit to 10 MB.
Changes the connection inactivity time-out to 15 minutes.
Set-SendConnector “Contoso.com Send Connector” -MaxMessageSize 10MB -ConnectionInactivityTimeOut
00:15:00
The FrontendProxyEnabled parameter routes outbound messages through the CAS server, where destination specific routing, such as DNS or IP address, is set, when the parameter is set to $true.
E
Need to disable the send connector from Chicago to the internet so that when a new send connector on the Baltimore server is created, email can be sent to the internet.
QUESTION 18
Drag and Drop Question
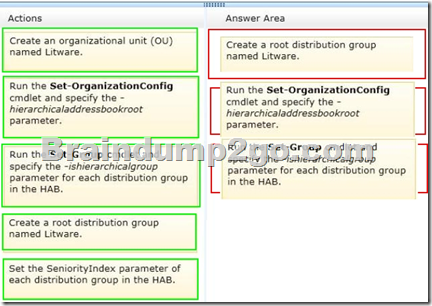
You need to create and configure a hierarchical address book (HAB) named Litware to reflect the company’s organizational chart.
Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
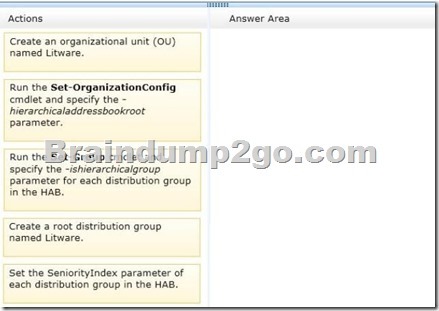
Answer:
QUESTION 19
Drag and Drop Question
You are planning the upgrade to Exchange Server 2013.
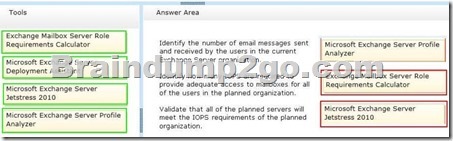
You plan to perform the following tasks:
– Identify the number of email messages sent and received by the users in the current Exchange Server organization.
– Identify how many IOPS are required to provide adequate access to mailboxes for all of the users in the planned organization.
– Validate that all of the planned servers will meet the IOPS requirements of the planned organization.
You need to identify which tool must be used to achieve each task.
Which tools should you identify? To answer, drag the appropriate tool to the correct task in the answer area. Each tool may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
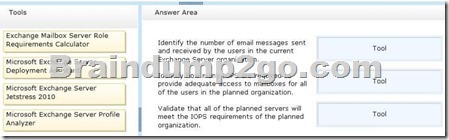
Answer:
QUESTION 20
You are testing the planned implementation of Exchange Server 2013.
After you begin moving several mailboxes to Exchange Server 2013, you discover that users on the internal network that have been moved are prompted repeatedly for their credentials when they run Microsoft Outlook.
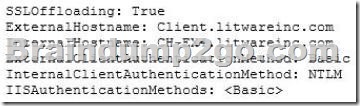
You run the Get-OutlookAnywhere cmdlet on CH-EX4, and receive the following output:
You need to prevent the internal users from being prompted for their credentials when they connect to their mailbox by using Outlook.
Which property should you modify by using the Set-OutlookAnywhere cmdlet?
A. IISAuthenticationMethods
B. InternalHostname
C. ExternalHostname
D. ExternalClientAuthenticationMethod
E. InternalClientAuthenticationMethod
Answer: A
Explanation:
InternalClientAuthenticationMethod is NTLM
Windows Challenge/Response (NTLM) is the authentication protocol used on networks that include systems running the Windows operating system and on stand-alone systems.
NTLM credentials are based on data obtained during the interactive logon process and consist of a domain name, a user name, and a one-way hash of the user’s password.
NEED TO CONVERT THE INTERNALCLIENTAUTHENTICATIONMETHOD TO BASIS NOT NTLM IN ORDER TO FIX THE ISSUE.
USE IISAUTHENTICATIONMETHODS PARAMETER IN ORDER TO ACHIEVE THIS.
Set-OutlookAnywhere
Use the Set-OutlookAnywhere cmdlet to modify the properties on a computer running Microsoft Exchange Server 2013 enabled for Microsoft Outlook Anywhere.
EXAMPLE 1
This example sets the client authentication method to NTLM for the /rpc virtual directory on the Client Access server CAS01.
Set-OutlookAnywhere -Identity:CAS01\rpc (Default Web Site) -ExternalClientAuthenticationMethod:Ntlm
PARAMETERS
The IISAuthenticationMethods parameter specifies the authentication method enabled on the /rpc virtual directory in Internet Information Services (IIS).
You can set the virtual directory to allow Basic authentication or NTLM authentication. Alternatively, you can also set the virtual directory to allow both Basic and NTLM authentication. All other authentication methods are disabled.
You may want to enable both Basic and NTLM authentication if you’re using the IIS virtual directory with multiple applications that require different authentication methods.
The InternalHostname parameter specifies the internal hostname for the Outlook Anywhere virtual directory.
The ExternalHostname parameter specifies the external host name to use in the Microsoft Outlook profiles for users enabled for Outlook Anywhere.
The ExternalClientAuthenticationMethod parameter specifies the authentication method used for external client authentication. Possible values include:
– Basic
– Digest
– Ntlm
– Fba
– WindowsIntegrated
– LiveIdFba
– LiveIdBasic
– LiveIdNegotiate
– WSSecurity
– Certificate
– NegoEx
– OAuth
– Adfs
– Kerberos
– Negotiate
– Misconfigured
The InternalClientAuthenticationMethod parameter
specifies the authentication method used for internal client authentication. Possible values include:
– Basic
– Digest
– Ntlm
– Fba
– WindowsIntegrated
– LiveIdFba
– LiveIdBasic
– LiveIdNegotiate
– WSSecurity
– Certificate
– NegoEx
– OAuth
– Adfs
– Kerberos
– Negotiate
– Misconfigured
Want to be 70-341 certified? Using Braindump2go New Released 70-341 Exam Dumps Now! We Promise you a 100% Success Passing Exam 70-341 Or We will return your money back instantly!